Самое актуальное и обсуждаемое
Популярное
Полезные советы

Важно знать!
37 неделя беременности
37 неделя беременности от зачатия
Что происходит с малышом на 37 неделе?
К 37 неделе беременности от зачатия ребенок считается полностью зрелым и доношенным. Все системы его организма готовы к жизни...
Читать далее
35 неделя беременности. календарь беременности
7 продуктов с высоким содержанием железа от анемии
32 неделя беременности: норма веса ребенка, что происходит с малышом и мамой, фото, развитие плода
36-я неделя беременности
33 неделя беременности
5 первых признаков родов, которые можно перепутать с ложными схватками
27 неделя беременности
8 признаков скрытого хронического воспаления
26 неделя беременности
Рекомендуем
Лучшее

Важно знать!
13 лучших заменителей сахара
Синтетические подсластители
Сукралоза – является синтетическим подсластителем, но абсолютно безопасным , она в 500 раз слаще сахара и не обладает калорийностью, за что ее очень любят спортсмены и производители...
Читать далее
39 неделя беременности
17 неделя беременности
8 признаков дефицита витамина d
10 эффективных способов зачать сына
40 советов как быстро не кончать мужчине, что делать, куда «бежать»
10 показателей. расшифровываем электрокардиограмму (экг)
7 проблем со здоровьем, которые могут быть причиной необъяснимых синяков на вашем теле
6 неделя беременности
10 полезных свойств кедровых орехов для человека и противопоказания
Обсуждаемое

Важно знать!
5 способов как можно определить беременность без теста
Как проверить беременность на ранних сроках в домашних условиях
В процессе планирования беременности метод определения базальной температуры рекомендуется врачами — гинекологами как один из наиболее достоверных...
Читать далее
3d узи
12 полезных и дешевых продуктов для набора мышечной массы
10 простых способов, как быстро и правильно почистить лимфу в домашних условиях
20 неделя беременности
12 лучших витаминов при планировании беременности
9 способов повышения “хорошего” холестерина
10 советов тренера для желающих похудеть
7 лучших диет 2021
46
Популярное
Актуальное

Важно знать!
45 слабительных продуктов, которые помогают избавиться от запоров
От каких продуктов крепится стул?
Каждый человек с легкостью усваивает закрепляющие продукты. Они расщепляются быстро, так как в этом им помогают ферменты, особенно желудочный сок. Затем происходит их...
Читать далее
30 недель беременности: сколько это месяцев и как их считать?
10 лучших витаминов для кормящих мам
10 удивительных изменений в организме, если начать пить вишневый сок
10 опасных глазных симптомов
10 упражнений и массаж глаз для восстановление зрения по методу жданова
18 потрясающих способов сбросить вес без физической нагрузки
6 фактов о сперме
16 продуктов богатых ниацином (витамином b3)
6 способов для родителей превратить гуление и агуканье младенца в речь
Обновления
 статьи
Зубные импланты: виды и материалы для изготовления
статьи
Зубные импланты: виды и материалы для изготовления
Какие бывают виды имплантации зубов.
При выборе техники оперативного вмешательства учитывают клинические...
 Как подобрать красивое название для группы?
Как подобрать красивое название для группы?
Начало пути…
В 1966 году The Yardbirds — группа Джимми Пейджа — потерпела крах… Так уж сложилось, что...
 Эпидемиолог рассказал, почему россия выглядит островком стабильности во время пандемии covid-19
Эпидемиолог рассказал, почему россия выглядит островком стабильности во время пандемии covid-19
Комментарий эксперта
Согласно восьмой версии постановления «Профилактика, диагностика и лечение новой...
 Вич
Вич
Частота симптомов и степени тяжести
Инкубационный период составляет от 2 до 14 суток, в среднем 5–7...
 Авокадо: польза и вред для организма человека
Авокадо: польза и вред для организма человека
Пересадка
Нужно запастись терпением и дождаться, пока косточка лопнет и на ней появятся ростки. Затем...
 Как отличить нейродермит от псориаза
Как отличить нейродермит от псориаза
Содержание статьи
Псориаз – это хроническая болезнь, которая поражает поверхность кожи, ногти, а...
 Деменция у пожилых людей: как ее распознать и приостановить и что делать, если недуг поразил близкого человека?
Деменция у пожилых людей: как ее распознать и приостановить и что делать, если недуг поразил близкого человека?
Другие формы слабоумия
Когда нейроны мозга поражаются в результате нарушенного кровообращения, говорят...
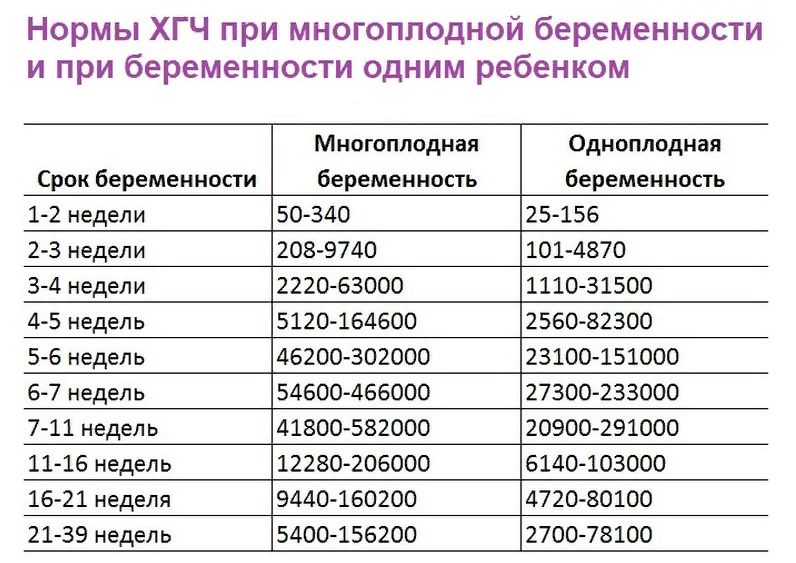
 Калькуляторы беременности
Калькуляторы беременности
Дополнительные способы
Акушерский срок сегодня считается самым точным, а остальные методы используются...
 Беременность
Беременность
Беременность
Беременность
Сомневаться или нет?
Точность подобного метода у некоторых может вызвать много сомнений, ведь не у всех...
 Хлоргексидин
Хлоргексидин
Инструкция по применению
Перед использованием любой из лекарственных форм необходимо изучить основные...
 Что за кошмар такой картинки трипофобии и как прекратить их бояться?
Что за кошмар такой картинки трипофобии и как прекратить их бояться?
Что такое трипофобия и кто такие трипофобы
Термин «трипофобия» происходит от гр. τρύπα — отверстие и...
 Синехии. информация для родителей
Синехии. информация для родителей
Бум лабиопластики и Папа римский. Что потом случилось с готтентотами
После прихода белых людей, местное...